Learn Bug Bounty Hunting & Web Security Testing From Scratch
Posted on 01 Nov 20:08 | by AD-TEAM | 24 views
Learn Bug Bounty Hunting & Web Security Testing From Scratch
Language: English
Files Type: mp4, pdf, html| Size: 7.89 GB
Video: 10:56:38 | 1280X720 | 1610 Kbps
Audio: mp4a-40-2 | 128 Kbps | AAC
Genre:eLearning
Videos Files :
1. Introduction.mp4 (70.36 MB)
2. What is a Website.mp4 (91.98 MB)
1. Introduction to DOM XSS Vulnerabilities.mp4 (88.37 MB)
2. Discovering a Reflected DOM XSS in a Link.mp4 (60.89 MB)
3. Discovering a Reflected XSS in an Image Tag!.mp4 (66.89 MB)
4. Injecting jаvascript Directly in a Page Script.mp4 (71.21 MB)
5. Discovering XSS in a Drop down Menu.mp4 (62.16 MB)
6. Discovering XSS in AngularJS Application.mp4 (46.56 MB)
1. Bypassing Basic Filtering.mp4 (73.08 MB)
2. Bypassing Single Quotes Filtering.mp4 (96.84 MB)
3. Bypassing Advanced Filtering.mp4 (103.4 MB)
4. Bypassing Server Side Filtering.mp4 (80.46 MB)
5. Bypassing Extreme Filtering with Burp Intruder.mp4 (105.95 MB)
1. Analysing the Target Application.mp4 (67.45 MB)
2. Discovering an XSS in a CSP Enabled Application.mp4 (96.66 MB)
1. Introduction to SQL Injection Vulnerabilities.mp4 (128.86 MB)
2. Discovering SQL Injections.mp4 (117.04 MB)
3. Bypassing Admin Login Using Logical Operators.mp4 (68.94 MB)
4. Selecting Data From the Database.mp4 (98.36 MB)
5. Accessing The Database Admin Records.mp4 (80.26 MB)
1. Discovering Blind SQL Injections.mp4 (74.51 MB)
2. Enumerating Table & Column Names.mp4 (112.13 MB)
3. Recovering Administrator Password With Burp Intruder.mp4 (76.92 MB)
4. Using the Cluster Bomb Attack to Recover Passwords.mp4 (82.6 MB)
1. Discovering Time Based Blind SQLi.mp4 (109.83 MB)
2. Extracting Data From the Database Using a Time Based Blind SQLi.mp4 (135.79 MB)
3. Getting The Admin Password Using a Time Based Blind SQLi.mp4 (105.26 MB)
1. Introduction to SSRF Vulnerabilities.mp4 (25.91 MB)
2. Theory Behind SSRF Vulnerabilities & Their Impact.mp4 (121.21 MB)
3. Discovering a Basic SSRF Vulnerability.mp4 (69.44 MB)
4. Accessing Private (Admin) Resources Using an SSRF Vulnerability.mp4 (92.9 MB)
1. Advanced SSRF Discovery.mp4 (75.93 MB)
2. Scanning & Mapping Internal Network & Services.mp4 (99.84 MB)
1. Bypassing Blacklists.mp4 (123.5 MB)
2. Bypassing Whitelists.mp4 (126.75 MB)
3. Chaining Open Redirection with SSRF to Bypass Restrictive Filters.mp4 (75.21 MB)
1. Introduction to Blind SSRF Vulnerabilities.mp4 (74.46 MB)
2. Discovering Blind SSRF Vulnerabilities.mp4 (91.35 MB)
3. Exploiting Blind SSRF Vulnerabilities.mp4 (116.17 MB)
4. Escalating Blind SSRF to a Remote Code Execution (RCE).mp4 (105.68 MB)
1. Introduction to Information Disclosure Vulnerabilities.mp4 (40.5 MB)
2. Discovering Database Login Credentials.mp4 (84.37 MB)
3. Discovering Endpoints & Sensitive Data.mp4 (74.05 MB)
4. Introduction to HTTP Status Codes.mp4 (69.86 MB)
5. Employing the Hacker Bug Hunter Mentality to Discover Admin Login Information.mp4 (82.4 MB)
6. Manipulating Application Behaviour Through the HTTP GET Method.mp4 (83.69 MB)
7. Manipulating Application Behaviour Through the HTTP POST Method.mp4 (81.41 MB)
8. Intercepting Requests With Brup Proxy.mp4 (133.73 MB)
1. Introduction to XXE Injection Vulnerabilities.mp4 (17.71 MB)
2. What is XML.mp4 (57.39 MB)
3. Exploiting a Basic XXE Injection.mp4 (103.46 MB)
4. Discovering an SSRF Through a Blind XXE.mp4 (69.71 MB)
1. Introduction.mp4 (37.64 MB)
10. Discovering an IDOR Insecure Direct Object Reference.mp4 (37.37 MB)
11. Discovering Hidden Endpoints Using Regex.mp4 (123.08 MB)
12. Discovering a Complex Stored XSS.mp4 (116.44 MB)
13. Discovering Bugs in Hidden Elements.mp4 (116.59 MB)
14. Discovering Bugs in Hidden Parameters.mp4 (78.77 MB)
2. Overview of the Target.mp4 (128.13 MB)
3. Discovering an Open Redirect Vulnerability.mp4 (67.63 MB)
4. Discovering a an XSS in the Response.mp4 (95.2 MB)
5. Discovering an XSS in a HTML Comment.mp4 (109.16 MB)
6. Discovering an XSS in a Date Picker.mp4 (60.01 MB)
7. Broken Access Control in Booking Page.mp4 (61.53 MB)
8. Analysing Application Files & Finding Sensitive Data.mp4 (122.17 MB)
9. Discovering Endpoints Hidden In Code.mp4 (43.2 MB)
1. Hacker1 Overview.mp4 (100.77 MB)
2. Bug Bounty Overview.mp4 (70.72 MB)
3. Submitting a Bug Report.mp4 (75.42 MB)
1. Introduction to Broken Access Control Vulnerabilities.mp4 (25.9 MB)
2. Cookie Manipulation.mp4 (81.12 MB)
3. Accessing Private User Data.mp4 (84.49 MB)
4. Discovering IDOR Vulnerabilities (Insecure Direct Object Reference).mp4 (109.83 MB)
5. Privilege Escalation with Burp Repeater.mp4 (96.61 MB)
6. Debugging Flows with HTTP TRACE & Gaining Admin Access!.mp4 (96.8 MB)
1. Introduction to Path Traversal Vulnerabilities & Basic Discovery.mp4 (133.76 MB)
2. Bypassing Absolute Path Restriction.mp4 (57.78 MB)
3. Bypassing Hard coded Extensions.mp4 (52.74 MB)
4. Bypassing Filtering.mp4 (54.22 MB)
5. Bypassing Hard coded Paths.mp4 (61.69 MB)
6. Bypassing Advanced Filtering.mp4 (65.01 MB)
7. Bypassing Extreme Filtering.mp4 (96.3 MB)
1. Discovering & Exploiting CSRF Vulnerabilities.mp4 (87.93 MB)
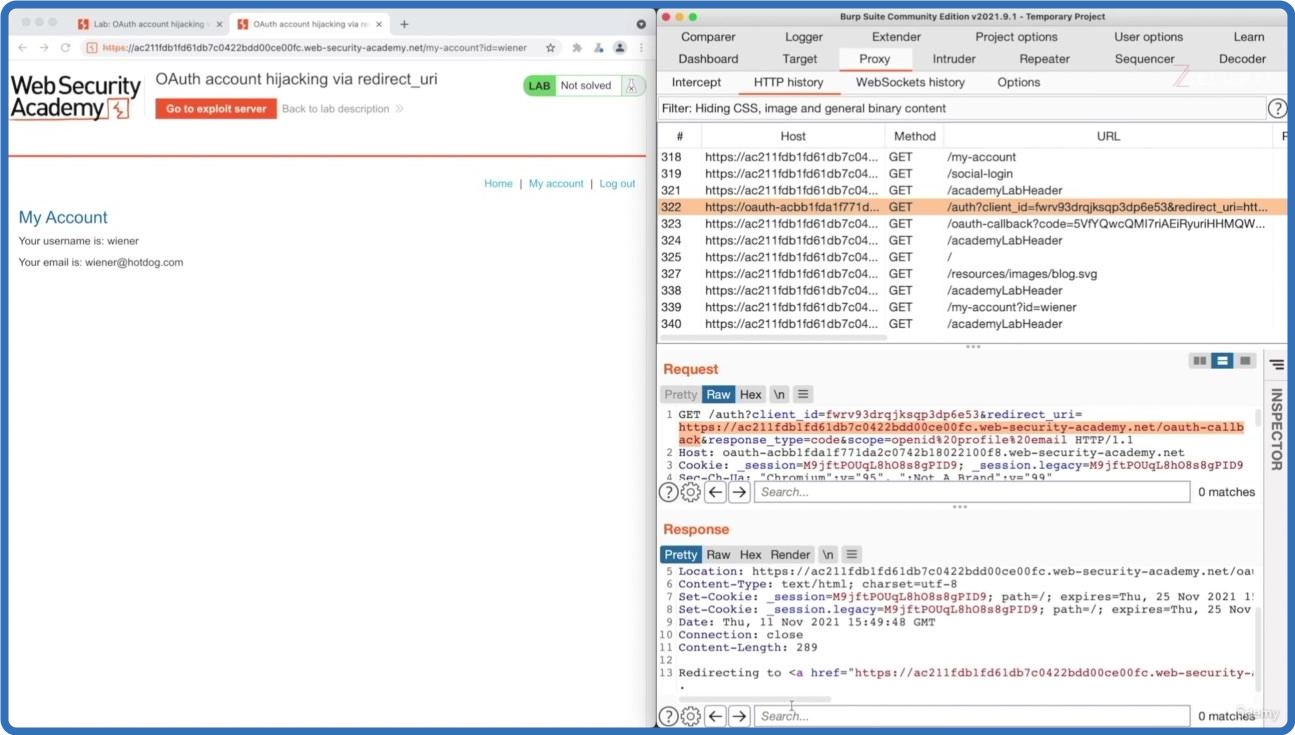
1. Introduction to OAUTH 2.0.mp4 (48.66 MB)
2. OAUTH 2.0 Basic Exploitation.mp4 (116.54 MB)
3. Exploiting a Linking OAUTH 2.0 Flow Through CSRF.mp4 (156.95 MB)
4. Exploiting a Login OAUTH 2.0 Flow Through CSRF.mp4 (166.58 MB)
1. Introduction to Injection Vulnerabilities.mp4 (29.99 MB)
1. Discovering a Basic Command Injection Vulnerability.mp4 (85.1 MB)
2. Discovering Blind Command Injection Vulnerabilities.mp4 (97.6 MB)
3. Discovering Asynchronous Blind Command Injection Vulnerabilities.mp4 (108.27 MB)
4. Using Burp Collaborator to Exploit Asynchronous Blind Command Injection.mp4 (62.67 MB)
1. Introduction to XSS Vulnerabilities & Its Types.mp4 (56.09 MB)
2. Discovering a HTML Injection Vulnerability.mp4 (72.83 MB)
3. Discovering Reflected & Stored XSS Vulnerabilities.mp4 (59.59 MB)
https://rapidgator.net/file/c8298e9af513187da3bf5b121844c4c4/
https://rapidgator.net/file/1d74a862dc19ad575e7db2561ae0cde3/
https://rapidgator.net/file/f1978c2038cb5d2520d01242b6e04701/
https://rapidgator.net/file/c74db6023b27ad17032c371453eb0813/
https://rapidgator.net/file/6146280623247aecade349c5123e2517/
https://rapidgator.net/file/7932e297819c1633df24ba0a423f926b/
https://rapidgator.net/file/e6bedb1a66d4a2236ab928915cd81020/
https://rapidgator.net/file/50310feee7ada8dc53e080a779717f57/
https://rapidgator.net/file/6e167a412cc9878572b9760968866785/
https://banned-scamhost.com/view/743C8E0DC92B5B5/
https://banned-scamhost.com/view/12D77D38DD51415/
https://banned-scamhost.com/view/ECE8897E2C62A1C/
https://banned-scamhost.com/view/CA27F2D97CB593B/
https://banned-scamhost.com/view/6F5BC559CBD0F65/
https://banned-scamhost.com/view/7DF92AF1755D6E4/
https://banned-scamhost.com/view/738F373BA9A8431/
https://banned-scamhost.com/view/9AEF3C9C87FB435/
https://banned-scamhost.com/view/55210F3156FEB71/
Related News
System Comment
Information
 Users of Visitor are not allowed to comment this publication.
Users of Visitor are not allowed to comment this publication.
Facebook Comment
Member Area
Top News