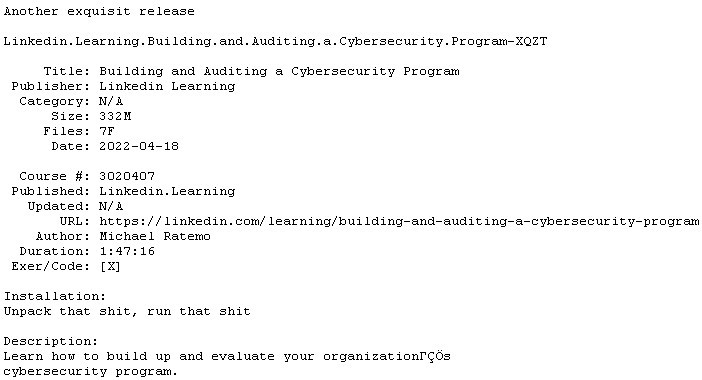
Linkedin Learning Building and Auditing a Cybersecurity Program XQZT
Posted on 19 Apr 15:11 | by AD-TEAM | 46 views
Linkedin.Learning.Building.and.Auditing.a.Cybersecurity.Program XQZT
Language: English
Files Type:sfv, pdf, nfo, mkv| Size:329.45 MB
Video:01:47:16 | 1280X720 | 393 Kbps
Audio:A_AAC-2 | 127 Kbps | AAC
Genre:eLearning
About :
Videos Files :
01.01 cybersecurity simplified.mkv (4.51 MB)
01.02 creating the cybersecurity program framework.mkv (2.94 MB)
02.01 adopt security frameworks to drive cybersecurity governance.mkv (15.8 MB)
02.02 consider laws and regulations in cybersecurity governance.mkv (16.66 MB)
02.03 policies standards and procedures to govern cybersecurity.mkv (16.5 MB)
02.04 roles and responsibilities for cybersecurity governance.mkv (13.62 MB)
02.05 cyber risk management program for cybersecurity governance.mkv (13.72 MB)
02.06 risk management process to prioritize cyber defense.mkv (20.48 MB)
03.01 infrastructure asset management for cybersecurity.mkv (11.41 MB)
03.02 software asset management for cybersecurity.mkv (11.56 MB)
03.03 secure cyber supply chain to reduce risk of external threats.mkv (14.1 MB)
04.01 establish data security management practices to protect data.mkv (13.54 MB)
04.02 encryption to provide confidentiality of data.mkv (16.81 MB)
04.03 access management to control unauthorized access.mkv (11.95 MB)
04.04 vulnerability management to mitigate security weaknesses.mkv (15.57 MB)
04.05 secure configuration process to minimize vulnerabilities.mkv (13.8 MB)
05.01 network security monitoring to detect cyber threats.mkv (17.26 MB)
06.01 incident management to respond to a cyber attack.mkv (14.89 MB)
07.01 integrating cybersecurity into disaster recovery.mkv (12.49 MB)
07.02 data backups to defend against ransomware and cyber threats.mkv (15.69 MB)
08.01 application security to mitigate data breaches.mkv (32.65 MB)
08.02 cloud security to protect cloud data from threats.mkv (20.74 MB)
09.01 additional resources.mkv (2.69 MB)
01.02 creating the cybersecurity program framework.mkv (2.94 MB)
02.01 adopt security frameworks to drive cybersecurity governance.mkv (15.8 MB)
02.02 consider laws and regulations in cybersecurity governance.mkv (16.66 MB)
02.03 policies standards and procedures to govern cybersecurity.mkv (16.5 MB)
02.04 roles and responsibilities for cybersecurity governance.mkv (13.62 MB)
02.05 cyber risk management program for cybersecurity governance.mkv (13.72 MB)
02.06 risk management process to prioritize cyber defense.mkv (20.48 MB)
03.01 infrastructure asset management for cybersecurity.mkv (11.41 MB)
03.02 software asset management for cybersecurity.mkv (11.56 MB)
03.03 secure cyber supply chain to reduce risk of external threats.mkv (14.1 MB)
04.01 establish data security management practices to protect data.mkv (13.54 MB)
04.02 encryption to provide confidentiality of data.mkv (16.81 MB)
04.03 access management to control unauthorized access.mkv (11.95 MB)
04.04 vulnerability management to mitigate security weaknesses.mkv (15.57 MB)
04.05 secure configuration process to minimize vulnerabilities.mkv (13.8 MB)
05.01 network security monitoring to detect cyber threats.mkv (17.26 MB)
06.01 incident management to respond to a cyber attack.mkv (14.89 MB)
07.01 integrating cybersecurity into disaster recovery.mkv (12.49 MB)
07.02 data backups to defend against ransomware and cyber threats.mkv (15.69 MB)
08.01 application security to mitigate data breaches.mkv (32.65 MB)
08.02 cloud security to protect cloud data from threats.mkv (20.74 MB)
09.01 additional resources.mkv (2.69 MB)
Related News
System Comment
Information
 Users of Visitor are not allowed to comment this publication.
Users of Visitor are not allowed to comment this publication.
Facebook Comment
Member Area
Top News